Cybersecurity professionals come from many walks of life with a diverse array of technical backgrounds and experiences. While each has a different perspective and strategy for managing security – all can agree that cybersecurity alert fatigue is problematic and false positives are the bane of their jobs.
Security teams are under enormous pressure to identify cyberattacks targeting their organization and stop them before they turn into breaches. But how does one do that when it’s harder than ever to distinguish between benign and malicious behavior? And chasing an ever-growing list of vulnerabilities and patches for systems is an ongoing battle that never ends.
And if that wasn’t bad enough, a recent survey by FireEye found that three in four analysts are worried about missing incidents.
Is it any wonder why cybersecurity folks are experiencing alert fatigue and burnout, and that they have high turnover rates?
Too Many Alerts, Not Enough Time
Cybersecurity professionals are using more tools than ever before to help stay ahead of threats – both internally and externally. This results in an overwhelming number of notifications that require further investigation.
- Security Tool Alerts – More security tools than ever before, each with its own metrics and thresholds for alerting
- Support Ticket Alerts – new tickets are opened for every issue and often filled with outdated information as soon as the ticket is created.
Previous EMA research identified that 64% of the security tickets generated per day were not being worked due to lack of manpower (and automation).
And a recent survey by Critical Start found that 49% of analysts turn off high-volume alerting features when there are too many alerts to process.
In addition to the overwhelming number of alerts, the lack of context from many of these alerts can be challenging for teams to construct correlation and decide whether the issue presents risk to the environment and how to proceed with fixing them.
This same research from Critical Start showed that a security analyst can spend as much as 25% of their time chasing false positives – and a typical organization wastes an estimated 300 hours per week or more.
Combine this with the pressures of keeping up with a constantly changing landscape – new threats, technologies, new laws and regulations, frameworks – it’s no wonder that people feel overloaded and become numb or switch off to the information around them.
Why You Should Care
For security teams struggling to keep up, the result of all this information means things can be overlooked due to the sheer volume which may result in compromises or breaches being missed. They become desensitized which leads to missed or ignored alerts and delayed responses.
There is also a financial impact to the organization due to the man-hours lost spent investigating alerts. And employees are burned out, stressed – and quitting their jobs. That is bad news for companies already struggling to hire qualified cybersecurity resources.
Reducing the Burnout
With all this in mind, how do you tackle the problem of cybersecurity alert fatigue? Let’s dig in.
-
Risk Prioritization
When too many alerts are clustered at or about the same level, a method is needed to prioritize risk responses and determine where to apply limited resources. Risk prioritization helps identify issues that would negatively impact the business operations now or in the future, thus requiring greater or faster attention for mitigation.
Vulnerability intelligence such as exploitability, possible risk, and impact to the organization should all be considered.
Critical alerts should stand out from the others so they aren’t missed and can be identified immediately. Applying a severity level is the first step in grouping vulnerabilities, the next is adding context around the exploitability of vulnerabilities and identifying the real-time risk.
While an organization may have tens, hundreds, or thousands of vulnerabilities, the highest risk issues share common elements.
- They have active exploits available on the internet or in exploit packs
- They are remotely exploitable
- They often result in arbitrary code execution
- They are being used in known exploit campaigns
- They have active advisories from vendors and regulating bodies
The additional layer of context surrounding the real risk of vulnerabilities helps curate, classify, and reduce the number of alerts. This gives teams the ability to reduce the “noisy” data and triage the critical alerts quickly.
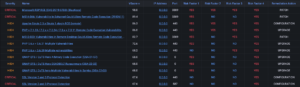
With a system like this, users can take action quickly just by someone mentioning that the alert is a “CRITICAL,” and doesn’t need a lengthy explanation.
This also helps to prioritize alerts for your on-call teams. For example, a less severe alert like a “LOW” can probably wait for operating hours while a “CRITICAL” or “HIGH” likely cannot.
-
Have a Clear Response and Resolution Strategy
Have a documented process for who is responsible for acting on alerts within a specified time as well as clear guidelines for escalating or transferring alerts to another party. Even the best alerting system can be exhausting if there is no way to close the loop.
Disposition actions may vary based on the nature of the assets that are impacted and the source of the vulnerability information. Acquiring a vendor-provided solution, changes in the configuration, application of workarounds, and just accepting the risk are all common risk dispositions. Documented processes will dictate the right security actions to take and will help lessen the load for those responsible for managing those alerts.
-
Keep Clear and Complete Documentation
Once an alert has been resolved, it’s time to shift to validation and documentation. As with all actions regarding vulnerabilities, the organization should retest the environment to ensure the control taken has resolved the issue as well as update the vulnerability’s record with the cause and the corrective actions taken. Additional instances of the vulnerability may indicate that the root cause has not been addressed, which may require additional corrective actions to be taken. Documentation will assist in this process.
Industry and compliance requirements such as for the payment card industry, healthcare, and others may provide additional guidance on what the organization must do as part of the documentation process.
Ultimately, your vulnerability management program is only as powerful as how well your vulnerabilities are resolved and what you can learn about your environment from the process.
-
Test Frequently and Thoroughly
It is important to understand whether or not the risk of the vulnerability has either been lessened or removed by the actions taken by retesting the environment. Monitoring for additional instances of the vulnerability through continuous assessments will ensure the corrective actions taken are effective. Teams often struggle to understand if the changes made have improved security or caused collateral damage to the network.
Plus, corporate networks are filled with users who install all kinds of software products and connect a myriad of devices which may have introduced additional vulnerabilities into the network.

-
Streamline Systems
Focus on automation to resolve as many of the “noise” alerts as possible. Machine learning and data intelligence can help adapt and sort through the influx of data and turn it into meaningful, digestible results. This gives teams time to take proactive action, instead of reacting to problems.
People resources should spend their time investigating and evaluating interesting alerts. Relying on automation is the key to fulfilling your team’s needs without adding to your payroll.
-
Know Your Obligations
Knowing the relevant obligations like PCI DSS or HIPAA can help employees cut through the noise and discern what is or is not relevant in the busy cybersecurity landscape.
The VULNERA Difference
For security teams managing the deluge of security alerts, VULNERA helps teams fight cybersecurity alert fatigue. Security assessments should empower you to improve the security of your organization, rather than drown you in alerts. That’s why our solutions help with the heavy-lifting so you can focus on remediation.
- Real-time Dashboard: Gives immediate insight into issues, assets, and services in internal, external, and cloud environments. Allows for additional analyst drill-downs and progress tracking.
- Remediation Tracking: Automated tracking monitors when issues are remediated and provides insight into why/how issues were closed.
- VSCORE Prioritization: Takes a risk-based approach to addressing the most critical vulnerabilities first and creates a prioritized roadmap for remediation.
- Vulnerability Management KPIs: Key performance indicators track overall vulnerability management program health (mean time to resolution, new vs. closed issues by day/month, etc.)
- Audit Reports: Satisfies the business and industry requirements for performance of vulnerability management and penetration testing.
Our customers report:
- A reduction in the number of alerts they receive as well as in the number of false positives
- Better quality alerts that are classified by risk level and provide context
- A reduction in the number of tools needed to manage their environment
- Ability to scale as the operation grows without having to add FTEs
- Less meetings to discuss current status of security issues and autotomy among members



